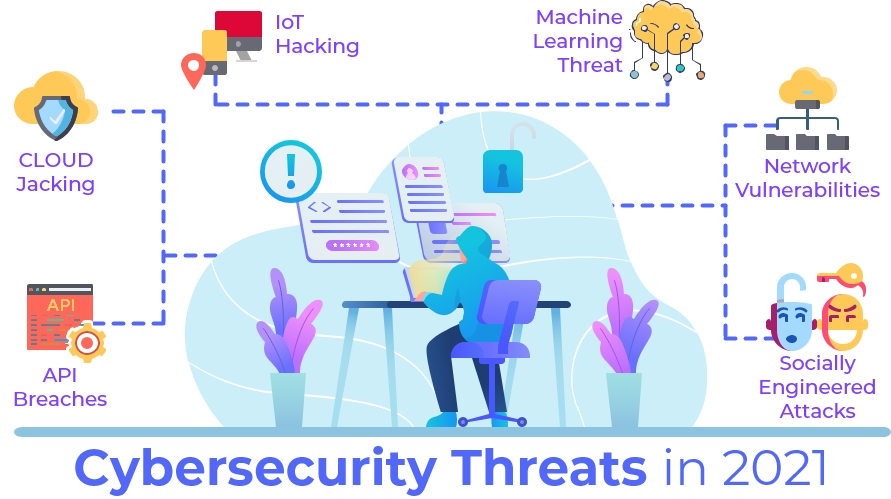
This unit describes the skills and knowledge required to gather data from various sources, analyse, and interpret information for threats, inconsistencies and discrepancies.
It applies to individuals who work in information technology security, including network and security specialists, and gather logs from devices, check abnormalities and respond accordingly. These individuals are responsible for supporting and preventing cyber threats attacking data in all business functions and in any industry context.
No licensing, legislative or certification requirements apply to this unit at the time of publication.
- Teacher: Liton Saha